XCOM file transfer
The XCOM file transfer protocol allows partners to transfer files securely and reliably over the internet. PGP is used to provide encryption of data between partners, and digital signing assures the identity of each partner.
This document defines Westpac's XCOM file transfer protocol. The intended audience of this document is:
- Server administrators who wish to use the provided command line scripts, and
- Software developers who wish to implement this messaging protocol in their software.
Security
All files transferred must be encrypted and digitally signed between Westpac and the customer's site. This serves two purposes; the first is to ensure that the data cannot be viewed by unauthorised sources. The second is to provide non-repudiation. Through the user of public/private keys, data can be digitally signed, by signing the file both Westpac and the customer can be assured that the data originated from a known source and it has not been tampered with.
Initial key exchange
To set up the XCOM transfer the customer will:
- Provide Westpac with the PGP public key used to verify the digital signature of the data file that is transferred between the customer and Westpac. Banking policy mandates that any file written to a hard drive in an untrusted zone (a server connected to an external network) must be PGP encrypted and digitally signed.
- Provide a username and password for Westpac to log onto the customerr XCOM server if Westpac is required to push files back to the customer.
In return Westpac will:
- Provide a username and password to log onto Westpac's XCOM server.
- Provide the customer with Westpac's PGP public key. This would be used by the customer to encrypt a file that is sent to Westpac (this customer signs the file with their private key.)
- Agree with the customer on the file naming convention and directory paths.
Pushing a file to Wesptac
To push a file to Westpac the sending site carries out the following steps:
- Encrypts the data using Westpac's public key and signs the encrypted data with it's private key. To ensure the data does not get corrupted, when messages are encrypted they must be ASCII armoured.
- The file is then given to the XCOM client for transmission. XCOM connects to the remote computer using the username/password that Westpac provided.
- Once it is connected, the file is transferred to the Westpac XCOM server into the agreed directory.
- Westpac detects the arrival of the file. The digital signature is checked against the customers previously supplied PGP public key. Once the security aspects of the file have been verified, it is then processed.
- Once the file has been processed, it will be deleted from the incoming directory on Westpac's XCOM server.
Westpac pushing a file to the customer
For Westpac to push a file to the customer the following steps are carried out:
- Westpac encrypts the data using the customer's public key and signs the encrypted data with it's private key. To ensure that data does not get corrupted, when messages are encrypted they must be ASCII armoured.
- The file is then given to the XCOM client for transmission. Westpac's XCOM server connects to the remote computer using the username/password that the customer provided.
- Once it is connected the file is transferred to the customer's XCOM server into the agreed directory.
- The customer detects the arrival of the file. The digital signature is checked against Westpac's previously supplied PGP public key. If this matches then the file is decrypted using the customer's private PGP key.
- Once the security aspects of the file has been verified, it is then preocessed.
Polling a file from Westpac
To poll a file from Westpac the polling site carries out the following steps:
- Westpac encrypts the file using the customer's public key, ASCII armours it and signs it with Westpac's private key and deposits it in a customer directory ready to be picked up.
- The customer's XCOM client connects to the remote computer using the username/password that Westpac provided.
- Once the customer connects, the customer performs a 'Retrieve' to fetch the file based on the agreed file naming convention.
- Once the customer has fetched the file back to their site they should check the digital signature and compare is against the Westpac's previously supplied PGP key. If this matches then the file is decrypted using the customer's private PGP key.
- Once the security aspects of the file have been verified, it is then processed.
- Westpac will keep the file on its XCOM server for 30 days. After 30 days, Westpac will automatically delete the file.
File and directory names
File names can be of any format as long as they do contain only standard ASCII characters that are valid for file names. Do not include spaces.
The destination directories of both Westpac and the customer sites must be agreed before transfer can take place.
Network connectivity
Transport mechanism
XCOM will function on a variety of platforms and IP based networks. This includes the Internet, Frame Rely and ISDN. Before you will be able to access Westpac's XCOM server you must provide the IP address of your server running your XCOM client.
Westpac will then modify its firewall to allow your server access to Westpac's XCOM server on port 8044. The customer may also need to engage their own network support staff to allow their XCOM client to connect on port 8044.
Addresses
Test
- To transmit to Westpac via the Internet you must configure XCOM to send to
ssiw.support.qvalent.com(203.39.159.31) on port8044. - To transmit to Westpac via a dedicated leased line (Frame relay, ISDN, dial or Ethernet) you must configure XCOM to send to 10.168.252.4 or port
8044.
Production
- To transmit to Westpac via the Internet you must configure XCOM to send to
ssiw.qvalent.com(192.170.86.151) on port8044. - To transmit to Westpac via a dedicated leased line (Frame relay, ISDN, dial or Ethernet) you must configure XCOM to send to
10.120.16.32or port8044.
Quick start
- Qvalent implementation consultant creates an iLink test account for the customer's technical contact.
- Customer contact completes iLink connectivity form in test iLink.
- Qvalent implementation consultant arranges configuration of the test iLink XCOM server.
- Customer configures 3rd party software.
- Customer codes XCOM scripts.
- Customer undertakes testing in the test environment.
- Once customer is satisfied that testing is complete a sign off email is required to progress into production.
- Qvalent implementation consultant creates an iLink production account for the customer's technical contact.
- Customer contact completes iLink connectivity form in production iLink.
- Qvalent implementation consultant arranges configuration of the production iLink XCOM server. 11.Customer tests the XCOM connection in the live environment.
- Once this testing is successful customers can perform low value live testing of the other Westpac products that are being implemented.
iLink connectivity setup
In the early stages of your Westpac project you will be asked to provide the contact details of the IT person who will be responsible for setting up your XCOM connection.
Once these details are received you will be provided with an iLink login to enter your IP addresses and public keys.
The iLink connectivity process has the following steps:
- The Qvalent implementation consultant will provide the user's technical contact with a login to the iLink test instance.
- Fill in the setup connectivity form and submit
- The iLink connectivity team will receive a notification when the form is completed and will configure the iLink XCOM server with the new details. Please allow up to 3 working days for this configuration.
- Once this configuration is complete a notification will be sent and the user will need to configure the connection details provided on the updated connectivity page.
- User to send in a test file to test the XCOM connection and PGP encryption. Once this is confirmed the use can also undertake any user acceptance testing relative to their implementation.
- Once the Qvalent implementation consultant has received confirmation that all relevant testing has been completed steps 1 - 5 will need to be repeated in the production environment.
iLink URLs
- Test -
https://ilink.support.qvalent.com - Production -
https://ilink.westpac.com.au
Setup connectivity form
To setup your connectivity, click the Connectivity menu option at the top of the screen, then click the Setup connectivity button. The Setup connectivity page will be displayed where you can enter the following details:
- Contact emails - Add any additional email addresses that should receive connectivity related emails.
- PGP key - Before files are sent via XCOM they are encrypted, the user's PGP public key is required to decrypt these files before processing them in the iLink messaging server.
- Your XCOM server details - The fields in this section are the details that iLink uses when connecting to the user's XCOM server to place files. The login provided for this connection will need to have privileges to write to the directory provided.
- IP addresses - The iLink solution has a white list of IP addresses accepted for each user. Users need to provide the IP address or addresses that their incoming requests will be coming from, this is the external IP address taking into account any proxy servers or other externally facing network infrastructure. This can be found by logging on to iLink on your XCOM server and taking the browser address shown in the IP addresses section of the connectivity form.
Once the iLink server configuration is complete the user will receive an email notifying them that they can begin testing. The user will then be able to see the iLink server details on the Connectivity details page.
- Westpac's key - This is the public PGP key that you will need to use to decrypt the files you receive from iLink.
- Your key - You can use these fields during testing to confirm which key you have loaded into iLink
- Westpac's XCOM server details - This section contains the XCOM username and password to enter to connect to the iLink XCOM server and the directory for placing customer iLink files.
- Your XCOM server details - This section contains the XCOM username and password for iLink to connect to your server and the directory for placing iLink customer files.
Software installation
The following software is required.
| Software | Description |
|---|---|
| CA-XCOM Unicenter Data Transport (version R11). | This is a commercial file transfer product created by Computer Associates (CA). Westpac will provide a copy to the customer. |
| PGP GNUPG (version 2.1.x). | GnuPG. This is a public domain PGP server that may be used free of charge. Obtaining of this product is the responsibility of the customer; however Westpac is able to provide technical assistance to support this. Gpg4win is the Windows binary containing GnuPG. |
Gpg4win
Use the latest version of Gpg4win.
Installing Gpg4win
Step 1: Run the installer and select your language.
Step 2: Select Next.
Step 3: Choose only the components: GnuPG, Kleopatra, GpgOL, GpgEX.
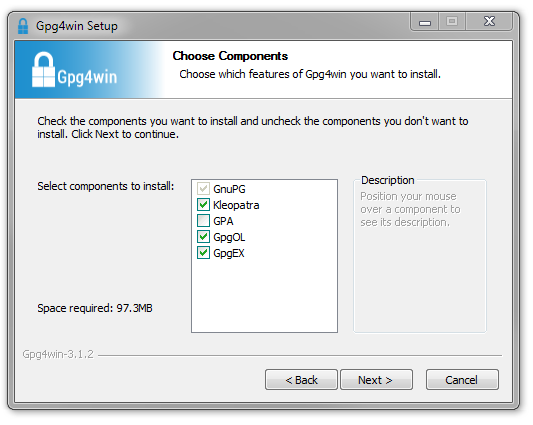
Step 4: Choose the install directory.
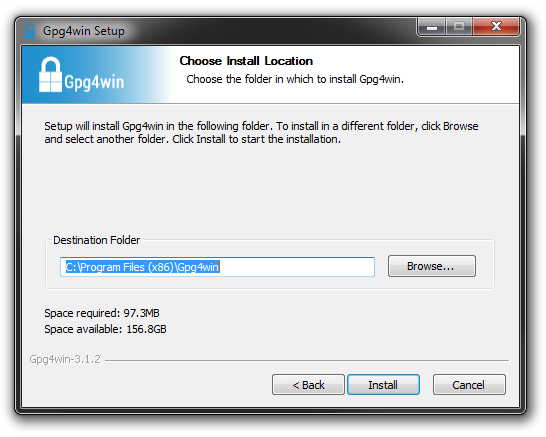
Click Install and follow the prompts.
Unicenter CA-XCOM Data Transport (version R11)
Artefacts
Advantage CA-XCOM Unicenter Data Transport (version R11) installation CD.
System requirements
Required OS for windows install:
- Windows 2003 Server.
Note: XCOM R11 will not install on a domain controller.
Install Notes
Ensure you have the correct version of XCOM. If you are installing XCOM on a server you need the server edition of XCOM. If you are installing it on a desktop you need the professional edition.
XCOM must be installed via the console or terminal services using the console switch i.e. mstsc /console <server.rdp>. XCOM will not install via a standard terminal server window.
Steps
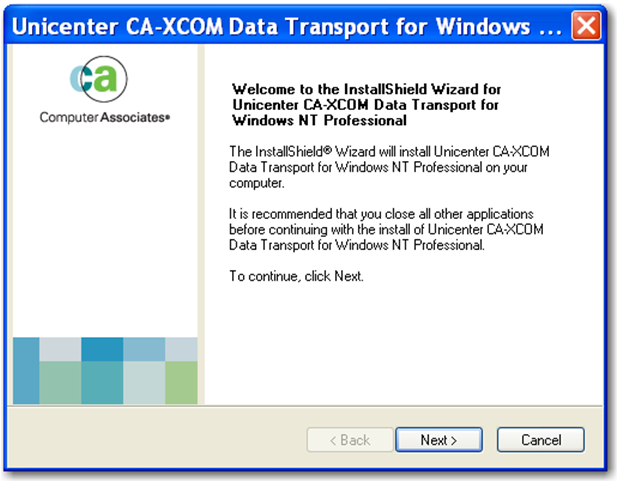
Step 1: Insert the Advantage CA-XCOM installation CD into the machine's CD-ROM drive. If the installation process does not start automatically, start it by running the 'setup.exe' executable in the root directory of the CD.
Step 2: Click 'Next'
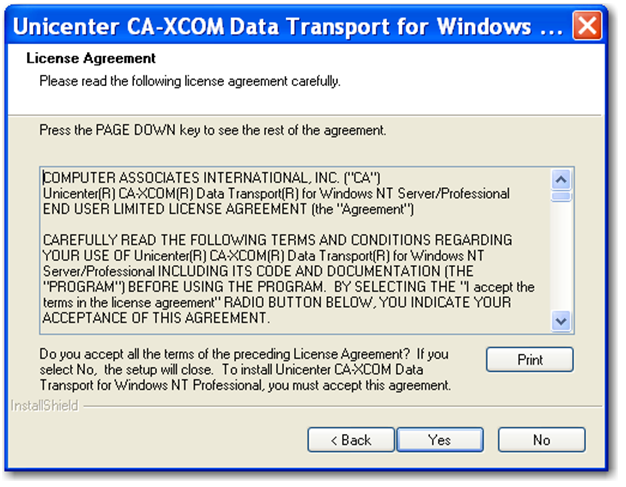
Step 3: Click 'Yes'
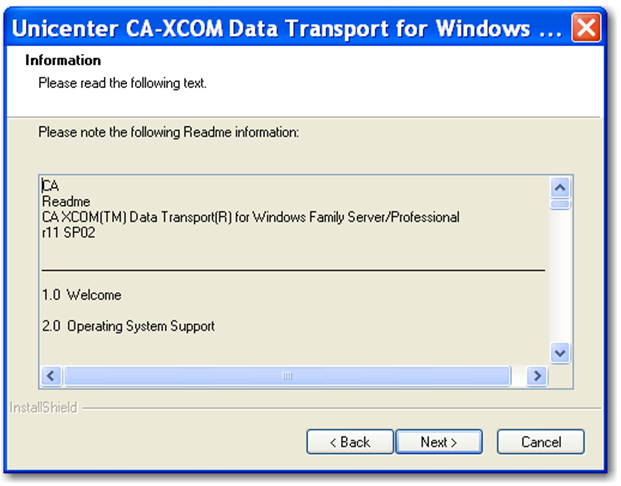
Step 4: Click 'Next'.
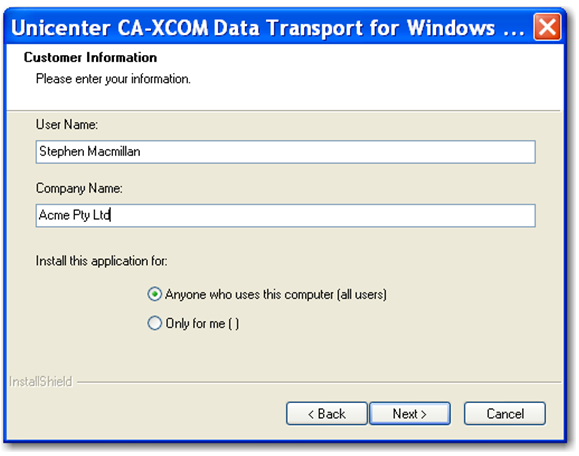
Step 5: Ensure the 'Anyone who uses this computer (all users)' radio button is selected, and click 'Next'.
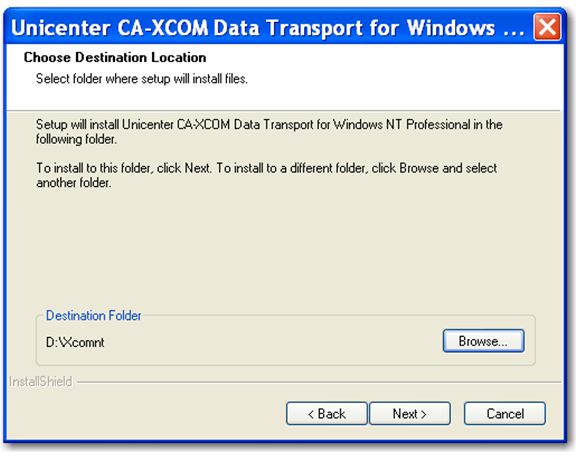
Step 6: Set the XCOM installation directory by clicking the 'Browse' button. The recommended installation directory for Unicenter CA-XCOM is 'D:\xcomnt'. If a different installation directory is chosen then record it for later use. Once the installation directory has been set, click 'Next'.
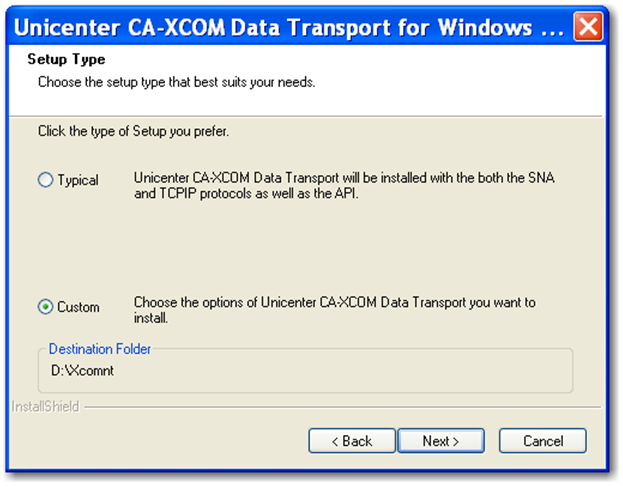
Step 7: Select 'Custom' and click 'Next'.
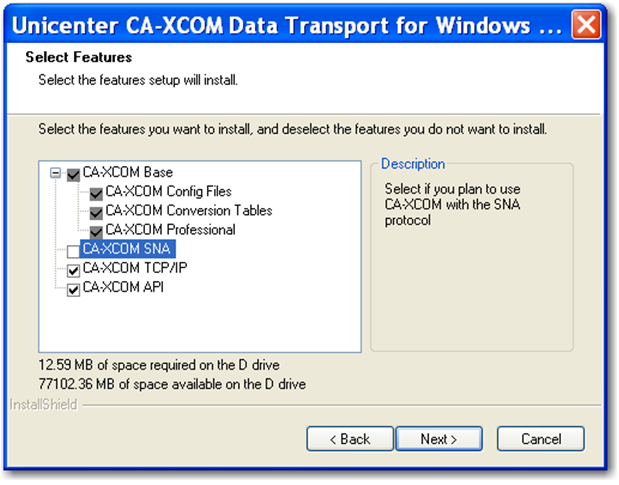
Step 8: Un-check the 'CA-XCOM SNA' checkbox and click 'Next'.
Step 9: Click 'Next'.
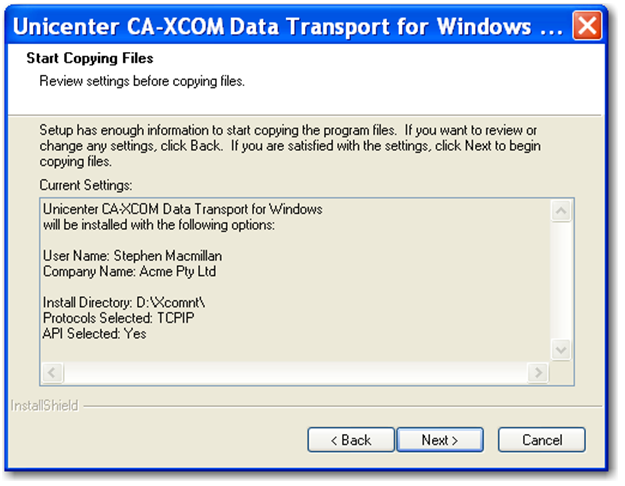
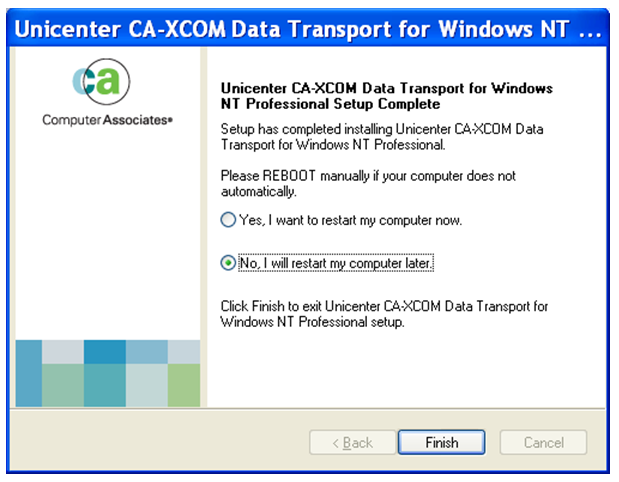
Step 10: When the installation is complete, select the 'No, I will restart my computer later' radio button and click 'Finish'.
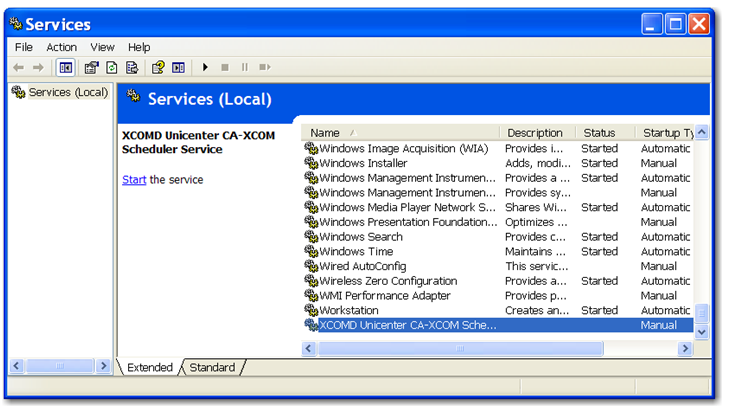
Step 11: Using the Windows Services configuration window, change the 'XCOMD Unicenter CAXCOM Scheduler Service' service to 'Automatic' start-up type.
Step 12: Restart the machine.
Verification
Check that the 'XCOMD Unicenter CA-XCOM Scheduler Service' exists in the list of system services, and is 'Started'.
CA-XCOM R11 Application configuration
- From the root directory of the CA-XCOM application installation, open the file
\config\xcom.glbin Notepad, (or your preferred text editor) - Set the value for the property
EXPIRATION_TIME=to600instead of the default6000 - A batch file can be set up to run upon XCOM successfully receiving a file. Set the value for the property
XPPCMD=to the name of the batch file to be run (full path required). - Set the value for the property
XCOM_USERID=to the empty string (ie. Nothing). - Save and close the file.
- Restart the "XCOMD Unicenter CA-XCOM Scheduler Service" Windows service.
- To obtain external access to the XCOM Client, a Windows User will need to be added to the Windows Operating System, as per details required by the external system, which the XCOM Client will be used to communicate with. This will be the XCOM username/password logon details used by external systems to communicate with your XCOM client.
Security permissions
In order for Westpac to send a file to your XCOM server you must provide Westpac with an account and password. This is a system level account i.e. Windows or Unix account.
The account must have enough privileges to do the following:
- Write to the directory where you installed XCOM. This is required to place the incoming data on the XCOM queue.
- Write to the directory where you require the incoming file to be placed. This is the directory where Westpac will tell XCOM to write the file.
GPG key generation
GnuPG RSA public/private key generation
Once GnuPG has been installed you need to generate a public key and private key. You will give the public key to partners you will exchange files with.
Both keys will be kept in your private and public key rings. Your private key ring will only contain your private key. Your public key ring will contain your own public key and the public keys of any other business partners (such as Westpac) who will provide your with their public key.
The steps are:
Step 1 - Create the Key Pair
The first step is to create:
- Your key rings.
- Your own public/private key pair.
Log onto the server that you installed GnuPG and change to the GnuPG installation directory.
Enter the following command:
C:\Program Files\GNU\GnuPG>gpg2 --gen-key
gpg2 (GnuPG) 2.1.0; Copyright (C) 2009 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Please select what kind of key you want:
(1) RSA and RSA (default)
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
Your selection? 1
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (2048)
Requested keysize is 2048 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0)
Key does not expire at all Is this correct? (y/N) y
You need a user ID to identify your key; the software constructs the user ID from the Real Name, Comment and Email Address in this form:
"Heinrich Heine (Der Dichter) <heinrichh@duesseldorf.de>"
Real name: Stephen Macmillan
Email address: smacmillan@acme.com
Comment: Acme
You selected this USER-ID:
"Stephen Macmillan (Acme) <smacmillan@acme.com>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? O
You need a Passphrase to protect your secret key.
We need to generate a lot of random bytes. It is a good idea to perform some other action (type on the keyboard, move the mouse, utilize the disks) during the prime genPassword1eration; this gives the random number generator a better chance to gain enough entropy.
+++++
+++++
We need to generate a lot of random bytes. It is a good idea to perform some other action (type on the keyboard, move the mouse, utilize the disks) during the prime generation; this gives the random number generator a better chance to gain enough entropy.
....+++++
+++++
gpg2: key 682B25F2 marked as ultimately trusted public and secret key created and signed.
gpg2: checking the trustdb gpg2: 3 marginal(s) needed, 1 complete(s) needed, PGP trust model
gpg2: depth: 0 valid: 1 signed: 0 trust: 0-, 0q, 0n, 0m, 0f, 1u pub 2048R/A28F9F1C 2010-01-22
Key fingerprint = 3230 E29F BA96 23D3 DA57 1D9E 204A B8F7 A28F 9F1C
uid Stephen Macmillan (Acme) <smacmillan@acme.com>
sub 2048R/E5CA1204 2010-01-22
C:\Program Files\GNU\GnuPG>Note that the pubring and secring are stored in the following locations. GPG2 knows these locations via the registry.
gpg2: keyring `C:\Users\StephenM\AppData\Roaming\gnupg\secring.
gpg2' created
gpg2: keyring `C:\Users\StephenM\AppData\Roaming\gnupg\pubring.
gpg2' createdTo specify a different location of the key rings, use the ``--homedir` parameter. Please make sure these files will not be removed/deleted.
Step 2 - Export your public key
Once the public and private keys are generated you need to export your public key and provide it to Westpac (or any other business partner you will be exchanging PGP encrypted data with).
From the command prompt, navigate to the GnuPG folder.
Issue the command
gpg2 --output <filename_to_write_exported_key_to> -a --export <id_of_key_to_export>To check if a PGP public key was generated
type <filename_specified_above>The output of these commands should be similar to:
gpg2 --output acme_pgp_pub_key.txt -a --export smac
millan@acme.com
type acme_pgp_pub_key.txt
-----BEGIN PGP PUBLIC KEY BLOCK-----
Version: GnuPG v2.0.17 (MingW32)
mQGiBENF9oYRBACsnPgVd5OpJWIk0QzKtQxB/rmz4fxvK/T9Tjct1QpKRf9F9it0
8nBRBydViILOnp5LjwcaUyE11I6tJtx4ziJEj6OXw2zEJZtemLHlEwnPz96Pv3yp
ICiAkJsjmD8W5anoQN73E7bPV6XomNq/qSoX7iJnothCGZwlMqTxxWmbywCgjjBU
oKopCad9DC2jW/X+rofE5HUD/j9lF5ViVehWT+Mv2is97j0HfTDuuSdvw/nAP0Gp
vg1T8f9HQtHD4Ws73z2Gp6sat5z9x30ytlkDkPkuUeV5qKgXnazV2TcQ3zy5WQL0
50BWXY9aXqupta5F0bhR50Py3AJd86ENOfgAti69BC2wYcxLyGeQYujYyy39Pz6q
ezDkA/9nSWMvORndzo1TPZ7GL3wPZZraYxHEsi66Vt38L+OKvawWwW/nFl7A7+n8
jjf/Kb5amrQuX4k0Nr3 5wZbYXZs8J9Q/j6etxpU2OmjoZ9A2DQ3PhUasa4HgjRLC
XljzwKdKQJKDUOa8TNpGrTepVYt39WJZoTcGv3yV4/4k+4mYcrQ0U3RlcGhlbiBN
YWNtaWxsYW4gKFF2YWxlbnQpIDxzbWFjbWlsbGFuQHF2YWxlbnQuY29tPohgBBMR
AgAgBQJDRfaGAhsDBgsJCAcDAgQVAggDBBYCAwECHgECF4AACgkQMRzcKAb3MX4e
GwCghCnjfAxV4gN2Ou4Khv1T0OWzzhEAoIIP9WR/ruH9IlNZ03Z4j5EG8t7guQEN
BENF9ocQBAChnSqMG3urBUDxdVT3o2vxFI6s3lj0VBtPPavx3iAWIJksF+xtfvSb
s478+V5frryeHZpOIZTpoOBF5+ndtfrMF1gI4uJbaEtqKBRRjvFY3pZ4qas3D9yP
qa2EgoU8PuNbYIXNGFLn2RbHA//AKlgjWYNEeQnIoOTO5bdv6tjHHwADBQP8DhuP
QHkbAQYgM4rJP6nOEk9tBbhEiCJTKcVHjb+FuTBc4/zkcUqDh7pE8AKSB2rNH2Zm
KIiBkWoPTcCch6cYE15Rsb4qo5FDamYo2nhmTW/uNANulDUbl4jOM6TzyAVtG1V4
3nVRcCx2z4VlLPN36hu/j7VKCbsMQyVXYyIiNmiISQQYEQIACQUCQ0X2hwIbDAAK
CRAxHNwoBvcxfuG3AJ4hGj/ry4Wy9TXCsXPkaTREcijh2ACfXoCWU36YM+S9yJqx
X4neR119XaM= =6k85
-----END PGP PUBLIC KEY BLOCK-----Upload this file using the iLink Connectivity Setup.
To check the fingerprint of your public key
gpg2 --fingerprint smacmillan@acme.comThe output should be similar to:
gpg2 --fingerprint smacmillan@acme.com
pub 2048R/A28F9F1C 2010-01-22
Key fingerprint = 3230 E29F BA96 23D3 DA57 1D9E 204A B8F7 A28F 9F1C
uid Stephen Macmillan (Acme) <smacmillan@acme.com>
sub 2048R/E5CA1204 2010-01-22The above fingerprint is 3230 E29F BA96 23D3 DA57 1D9E 204A B8F7 A28F 9F1C.
Step 3 - Import Westpac's public key
Westpac will provide you with their public key to import into your public key ring. This is Qvalent's public key. This is a 2-step process. You firstly import the key then you digitally sign it to indicate that you trust the key.
To import the Qvalent public key
gpg2 --import <filename_of_file_containing_qvalent_public_key> [Enter]To verify the key was added to the keystore correctly, list the public keys in the public keyring
gpg2 --list-keysThe output from the above two steps should be similar to:
gpg2 --import 17155x01_qvalent_pub_key.asc
gpg2: key C2E36CC8: public key "17155x01" imported
gpg2: Total number processed: 1
gpg2: imported: 1
gpg2 --list-keys
C:/Documents and Settings/user/Application Data/gnupg\pubring.gpg2
-------------------------------------------------------------------
pub 2048R/A28F9F1C 2010-01-22
uid Stephen Macmillan (Acme) <smacmillan@acme.com>
sub 2048R/E5CA1204 2010-01-22
pub 1024D/C2E36CC8 2001-10-15
uid 17155x01
sub 2048g/2E52ED13 2001-10-15The Qvalent public key needs to be validated (assuming the imported key id was imported_key).
Validate the key
gpg2 --edit-key imported_keyYou should receive some text on screen and them a prompt that looks like:
Command>
At the Command> prompt within gpg2, type the following
sign
You should verify at this step that the Qvalent key is valid and that the key you are signing with is the key generated in the previous section. If you are confident of this, enter Y to sign the key.
Enter the passphrase of the keys generated in the Step 1.
Gpg2 will then take you back to the Command> prompt once completed.
At the Command> prompt press q to quit.
When asked to confirm the changes, press Y.
The output from these steps should be similar to:
gpg2 --edit-key test@qvalent.com
gpg2 (GnuPG) 2.1.0; Copyright (C) 2009 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
pub 1024D/AD8A9D42 created: 2001-11-01 expires: never usage: SCA
trust: unknown validity: unknown
sub 1024g/26787C6E created: 2001-11-01 expires: never usage: E
[ unknown] (1). test <test@qvalent.com>
Command> sign
pub 1024D/AD8A9D42 created: 2001-11-01 expires: never usage: SCA
trust: unknown validity: unknown
Primary key fingerprint: D732 F115 31BE 2DE1 40C9 185F 07F8 8DFE AD8A 9D42
test <test@qvalent.com>
Are you sure that you want to sign this key with your
key "Stephen Macmillan (Acme) <smacmillan@acme.com>" (A28F9F1C)
Really sign? (y/N) y
You need a passphrase to unlock the secret key for
user: "Stephen Macmillan (Acme) <smacmillan@acme.com>"
2048-bit RSA key, ID A28F9F1C, created 2010-01-22
Command> q
Save changes? (y/N) yDecrypt a file using GnuPG
Decrypt an incoming file
gpg2 --output <filename_to_write_plaintext> --decrypt <filename_of_encrypted_data>Enter password for private key.
Decrypt an incoming file in a batch-type environment
gpg2 --yes --output [filename_to_write_plaintext] --batch --passphrase-fd 0 --homedir [path_of_keyrings] --decrypt [filename_of_encrypted_data] <[filename_of_file_containing_password]An example of a batch file to do this would consist of:
gpg2 --y --output test_dec.txt --batch --passphrase-fd 0 --decrypt example.txt.asc <password.txtwhere password.txt contains your PGP private key password and is piped into the gpg2 command.
The output when this batch file is executed would be:
dec.bat
gpg2 --y --output test_dec.txt --batch --passphrase-fd 0 --decrypt test.asc <password.txt
gpg2: encrypted with 2048-bit ELG-E key, ID 2E52ED13, created 2001-10-15
"17155x01"
gpg2: encrypted with 2048-bit ELG-E key, ID C45CC395, created 2005-10-07
"Stephen Macmillan (Acme) <smacmillan@acme.com>"
gpg2: Signature made 10/07/05 15:49:30 using DSA key ID C2E36CC8
gpg2: Good signature from "17155x01"Encrypt, sign and ASCII armour a file
Encrypt (and sign) data to send to Westpac (assume recipient key id is imported_Westpac_key, and your local key-pair id is local_key).
To encrypt and sign a file
gpg2 --compress-algo 1 --cipher-algo cast5 --armor --recipient imported_Westpac_key --local-user local_key --output <filename_to_write_encrypted_data> -se <filename_containing_data_to_encrypt>Enter password for private key.
Encrypt an outgoing file in a batch-type environment
gpg2 --compress-algo 1 --cipher-algo cast5 --passphrase-fd 0 --homedir [path_of_keyrings] --armor --recipient imported_Westpac_key --local-user local_key --output [filename_to_write_encrypted_data] -se [filename_containing_data_to_encrypt] <[filename_of_file_containing_password]An example of a batch file to do this would consist of:
gpg2 --compress-algo 1 --cipher-algo cast5 --passphrase-fd 0 --armor --recipient 17155x01 --local-user smacmillan@acme.com --output test_enc.asc -se test.txt <password.txtwhere password.txt contains your PGP private key password and is piped into the gpg2 command.
The output when this batch file is executed would be similar to:
enc.bat
gpg2 --compress-algo 1 --cipher-algo cast5 --passphras e-fd 0 --armor --recipient 17155x01 --local-user smacmillan@acme.com --output test_enc.asc -se test.txt <password.txt
Reading passphrase from file descriptor 0
You need a passphrase to unlock the secret key for
user: "Stephen Macmillan (Acme) <smacmillan@acme.com>"
2048-bit RSA key, ID A28F9F1C, created 2010-01-22
gpg2: checking the trustdb
gpg2: 3 marginal(s) needed, 1 complete(s) needed, PGP trust model
gpg2: depth: 0 valid: 1 signed: 1 trust: 0-, 0q, 0n, 0m, 0f, 1u
gpg2: depth: 1 valid: 1 signed: 0 trust: 1-, 0q, 0n, 0m, 0f, 0u
D:\Program Files\GNU\GnuPG>type test_enc.asc
-----BEGIN PGP MESSAGE-----
Version: GnuPG v2.0.17 (MingW32)
hQIOA38v4qEuUu0TEAf+IReSHiRz+v8Rfl6cqOJKxA/LRgY+3N24UnNIqXyDjuId
+rvCkgsgS2XJn6gukYXtsI7BaxNGGHvbKRaGb6XbcL62SW7lQol5a8N2uWai6wE/
qjILdOvDOpD6oqfMnk8CntVb4mIXJcQi+z6W+lJAHtHkJN2R8BRDoyqdTypIdJ+U
Z0sk1EjbZXVV1gJTj+uVy3LDvUiMOB1XMJn06lxz2nZQs4uzgRjqeGlI9x8HZS3d
tI5fz39hwZ4sn7CHDJ8qjhfxlo5U+Ebc7hwdhsD/OiAMbfcey96F+NjL0MVmNjr/
+vJ6Qgn9mIlcCZIWJT1cSOrogqrJMeWPY0KCrqXCXwf/eSBO/Rs/dDuyGDNIIhj3
do1xL4wbPUNtccwvqivPX8Q5dZPDBsH98VvIDaloHZuyeupO7gwkpS3zuesrB75L
JDbzVCgXEvXrS00CMi/on2R66gsBaEHmwGzaMLHVBTavrImWmR1kvL6CYMufloYg
MXbHF0ACEtR5DZ4PX6262OlnLKI+5St9EJ48zaYeJRT691IUqKqUIYNW9lnwOd7V
jjeA12iT74OPSAvzm6alAfN0Vz483vZdlavnid2Q/ijy2/PMA8ejZBqBs/idptej
Th5AuZcO9TI0tQEcyFxxIXM1AM/iZOhQUmvwAUGQWThta8Ri8fdhraupYyA5bZ0o
8MlzLRSAGO31hXLlBXUBUBH/4uhXpvE7n7dylCd8YDGl0ZAgypxQiuSGKzx01+s1
y1GHxP+xfo9dQaxqWbAtNfkf3hS3diz15T/URPKT0fFUe0gAsyH62CbahhOF/MJA
d9MF/0it3GwrDF5zHPC7tX7mJ8Nv2w== =mbYr
-----END PGP MESSAGE-----Testing the XCOM connection
The next step is to test the connectivity between your XCOM client and Westpac. Before doing this please confirm the following:
- You have provided your server's IP address and Westpac has confirmed that it has allowed that address through its firewall on port 8044.
- You have allowed your server to communicate on port 8044 through your own firewalls.
- You have provided your PGP public key to Westpac.
- Westpac has provided you with their PGP public key.
- Westpac has provided you with an XCOM username and password.
To test the connection via the Internet or leased line
To first check that you have connectivity try the following from your XCOM client:
- Open a command prompt (cmd.exe)
- Depending on your network path try the following telnet command:
- Via Internet try: telnet ssiw.qvalent.com 8044
- Via Leased line try: telnet 10.120.16.32 8044
If you get a connection the screen should look like:
_
(blank screen with flashing cursor in top left hand corner)If the screen looks like:
H:\>telnet ssiw.qvalent.com 8044
Connecting To ssiw.qvalent.com...Could not open connection to the host, on port
8044: Connect failedThen you can not establish a connection so consult with your network personnel. This could mean one of a couple of things. If you are connecting to the TEST environment (ssiw.support.qvalent.com) then it could mean that you have not opened your firewall for outbound connections. Westpac has no firewall restrictions on connections from the internet to its test environment.
If you are connecting to production, then you must provide Westpac with your production IP address as you must open your own firewall and Westpac need to open there's as well. The IP address must be provided 5 days in advance before the go live date.
To send a test transmission use a command similar to:
d:\xcomnt\xcomtcp.exe -c1 -f REMOTE_SYSTEM=<Westpac_ip_address> PORT=8044
USERID=<user> PASSWORD=<password>
REMOTE_FILE=<directory\file_to_write_into> PROTOCOL=TCPIP FILE_OPTION=CREATE
TRANSFERIDENTIFIER=FILE QUEUE=NO COMPRESS=NO LOCAL_FILE=<file_to_send>Note: If your XCOM server is in a windows domain then please refer to FAQ section.
An example XCOM transfer is similar to:
D:\pgp_scripts>d:\xcomnt\xcomtcp.exe -c1 -f REMOTE_SYSTEM=ssiw.qvalent.com
PORT=8044 USERID=testuser PASSWORD=xxxxxx REMOTE_FILE=test\test_file.txt.asc
PROTOCOL=TCPIP FILE_OPTION=CREATE TRANSFERIDENTIFIER=FILE QUEUE=NO COMPRESS=NO
LOCAL_FILE=test_file.txt.asc
(c) 2002 Computer Associates International, Inc. (CA).
05/10/14 11:49:14 TID=000003 [test_file.txt.asc --> test\test_file.txt.asc at qv
ts3]
XCOMN0029I Locally initiated transfer started.
05/10/14 11:49:18 TID=000003
XCOMN0011I Transfer ended; 19 records (1030 bytes) transmitted in 4 seconds
(257 bytes/second)
D:\pgp_scripts>File transmission
To send a file via XCOM
d:\xcomnt\xcomtcp.exe -c1 -f REMOTE_SYSTEM=<remote_system_ip_address> PORT=8044 USERID=<Westpac_assigned_username> PASSWORD=<Westpac_assigned_password> REMOTE_FILE=remoteDir\remoteFilename.txt PROTOCOL=TCPIP FILE_OPTION=CREATE TRANSFERIDENTIFIER=FILE QUEUE=NO COMPRESS=NO LOCAL_FILE=localFilename.txtTo retrieve a file via XCOM
d:\xcomnt\xcomtcp.exe -c4 -f REMOTE_SYSTEM_RF=<Westpac_ip_address> PORT=8044 USERID=<Westpac_assigned_username> PASSWORD=<Westpac_assigned_password> REMOTE_FILE_RF=<file_to_retrieve> PROTOCOL=TCPIP TRANSFERIDENTIFIER=RETRIEVE QUEUE=NO FILE_OPTION_RF=CREATE LOCAL_FILE_RF=<file_to_write_retrieved_data_to>the <file_to_retrieve> will be \\nas\Production\XcomRetrieve\<CustomerDir>\<filename> i.e. \\nas\Production\XcomRetrieve\Acme\Recall20080815.txt.asc
XCOM receiving command file
An example command file that gets executed by the XCOM client when it receives a file:
echo This batch file should only be opened using an XCom program, as the parameters that are required are very specific!
rem ---------------------------------------------------------------------------
rem Application and Resource locations
rem ---------------------------------------------------------------------------
SET JAVA_HOME=e:\jdk1.3
SET JARS_FOLDER=e:\FileTransfer\jars
rem ---------------------------------------------------------------------------
rem Property file location (fully qualified)
rem ---------------------------------------------------------------------------
SET PROPERTIES_FILENAME=e:\FileTransfer\cte_filetransfer_adapter.properties
rem ---------------------------------------------------------------------------
rem Class files
rem ---------------------------------------------------------------------------
SET DEPENDENT_JARS=%JARS_FOLDER%\xerces.jar;%JARS_FOLDER%\xalan.jar;%JARS_FOLDER%\ctcore.jar;%JARS_FOLDER%\jcert.jar;%JARS_FOLDER%\jnet.jar;%JARS_FOLDER%\jsse.jar;%JARS_FOLDER%\xp.jar;%JARS_FOLDER%\ConnectorCore.jar
rem ---------------------------------------------------------------------------
rem Get the parameters we need
rem ---------------------------------------------------------------------------
rem Get the Transaction ID (13th parameter)
SHIFT /1
SHIFT /1
SHIFT /1
SHIFT /1
SHIFT /1
SHIFT /1
SHIFT /1
SHIFT /1
SHIFT /1
SHIFT /1
SHIFT /1
SHIFT /1
rem Get the Received filename (20th parameter)
SHIFT /2
SHIFT /2
SHIFT /2
SHIFT /2
SHIFT /2
SHIFT /2
%JAVA_HOME%\bin\java -mx800m -ms16m -classpath %DEPENDENT_JARS% com.Westpac.exchange.connector.xcom.ReceiveNewFile %PROPERTIES_FILENAME% %1 %2Error handling
From a batch file you should always check the error level after the xcom call to ensure that the transfer was successful. Sample pseudo code for the batch file would be:
d:\xcomnt\xcomtcp.exe -c1 -f REMOTE_SYSTEM=ssiw.qvalent.com PORT=8044 USERID=testuser PASSWORD=xxxxxx REMOTE_FILE=test\test_file.txt.asc PROTOCOL=TCPIP FILE_OPTION=CREATE TRANSFERIDENTIFIER=FILE QUEUE=NO COMPRESS=NO LOCAL_FILE=test_file.txt.asc >> output.txt
if %ERRORLEVEL% NEQ 0 GTOTO ERROR
echo Successful Transmission
exit
ERROR:
Echo Bad Transmission
email output.txt to support personnelFAQ
Common XCOM error messages
If the XCOM error message looks like:
(Standard Output Stream...)
(Error Stream...)
Copyright (c) 1992, 1996 Computer Associates International, Inc.
All rights reserved.
03/04/14 10:52:51 TID=020485 [<filename> --> <filename> at <ip_address>]
XCOMN0029I Locally initiated transfer started.
03/04/14 10:52:52 TID=020485
#XCOMN0298E Unable to allocate remote transaction program: Txpi 211: Socket connect error return value = 10061This means that your XCOM client could not obtain a connection to the external XCOM client. This will be due to either a network issue, or the external system's XCOM client service not running.
If the XCOM error message looks like:
2008/02/11 18:18:12 TID=004413 PRG=xcomtcp PID=4904 IP=192.168.80.111
XCOMN0805I TCP/IP Connection Ended.
2008/02/11 18:18:12 TID=004413
XCOMN0288E System function failedThis means that when Westpac sends you a file the batch job you has specified in the <xcom install directory>\Config\xcom.glb i.e.
XPPCMD=e:\FileTransfer\ReceivedNewXComFile.bat
is failing to execute correctly and terminating abnormally. To debug the issue edit the xcom.glb file and change:
SHELL_CMD="cmd.exe" "/c" To SHELL_CMD="cmd.exe" "/k"- Restart the XCOM service
This will cause the DOS box to stay on the screen when the batch file runs when a file is received. Log into the server using the console and you will be able to see what is causing the error in your batch file. When it is fixed ensure that you set SHELL_CMD back to the /c switch to prevent the dialog boxes staying on the console.
XCOM will not install via terminal services
Please see section Install Notes.
What Platforms is XCOM available for?
Please consult the following link: http://supportconnectw.ca.com/public/xcom/infodocs/ca-xcom_verschart.asp
XCOM User Account / Windows Domains
When you create an XCOM user account under Windows NT it must be a local user on the server XCOM is installed and not a domain user account.
It is also advisable that you create an 'XCOM User Group' and place this user into this group. For NT2000 and NT2003, ensure that the 'XCOM User Group' has sufficient privileges to read & write files and execute scripts on the disk(s) where XCOM is installed or files will be accessed (such as the batch file that is called when a file is received).
Try logging into the server using the just created XCOM user to ensure that there was no typo's with the username or password.
If you are using NT2003, ensure that the 'XCOM User Group' has the security rights to 'Access this computer from the network'.
If your xcom server is in a windows domain you must use the command line parameter
DOMAIN= (blank space following equals sign) when sending to Westpac i.e.
d:\xcomnt\xcomtcp.exe -c1 -f DOMAIN= REMOTE_SYSTEM=<remote_ip_address>
PORT=8044 USERID=<Westpac_assigned_username>
PASSWORD=<Westpac_assigned_password> REMOTE_FILE=remoteDir\remoteFilename.txt
PROTOCOL=TCPIP FILE_OPTION=CREATE TRANSFERIDENTIFIER=FILE QUEUE=NO
COMPRESS=NO LOCAL_FILE=localFilename.txtIf you do not use this you will receive an "error setting the remote user id" from Westpac as your xcom server will be passing its domain name with its user name and Westpac will reject it.
GPG2 questions
When I decrypt a file with GPG2 I get the following WARNING:
gpg2: encrypted with 2048-bit ELG-E key, ID 2E52ED13, created 2001-10-15
"17155x01"
gpg2: encrypted with 1024-bit ELG-E key, ID C45CC395, created 2005-10-07
"Stephen Macmillan (Westpac) <smacmillan@qvalent.com>"
gpg2: Signature made 10/07/05 15:49:30 using DSA key ID C2E36CC8
gpg2: Good signature from "17155x01"
gpg2: WARNING: message was not integrity protectedThis is a compatibility issue between GPG2 and eBusiness server and can be ignored. The important line to note is "Good signature from 17155x01" This tells you that the file has not been tampered with.
When I encrypt a file using GPG2 I receive the following WARNING even though I have imported Westpac's key and signed it:
It is NOT certain that the key belongs to the person named in the user ID. If you *really* know what you are doing, you may answer the next question with yes.
Use this key anyway? (y/N)Try setting the trust level on the key using the command:
Gpg2 -edit-key <key name>Set the trust level to ultimate.
When I encrypt a file using a batch program with GPG2 and the file already exists the batch job stops and prompts me to about replacing the file:
File 'XXX.asc' exists. Overwrite? (y/N)Try using the parameter --yes on your GPG2 encrypt / decrypt command line. This will automatically answer 'Yes' for most questions GPG2 prompts for i.e.
gpg2 --yes --output [filename_to_write_plaintext] --batch --passphrase-fd 0 --homedir
[path_of_keyrings] --decrypt [filename_of_encrypted_data]
<[filename_of_file_containing_password]I'm having trouble connecting to Westpac's test or production environments, what should I try?
Refer to Testing the XCOM Connection.
Can a file be encrypted with more than one public key?
Yes! Westpac always encrypts files that it is sending to customers with both the customers public key and Westpac's public key. This allows a customer that is having difficulty decrypting a file (it may have become corrupted in transit) to send it back to Westpac to test decrypting it.
How can a file be encrypted with more that one public key? Doesn't this make the file twice as big?
No.
When GPG2 encrypts a file it generates a random session key and uses this random key to do the actual encryption. It then encrypts this session key with the recipient's public key and appends this data to the encrypted file. As Westpac always encrypts an outbound file with its own public key, the session key is also encrypted with Westpac's public key and this data is also added to the encrypted file.
So encrypting with additional public keys only makes the file slightly larger. By doing this either the recipient or Westpac can use their private key to decrypt the session key which inturn is used to decrypt the file.
When I receive an encrypted file how do I know what public key(s) it has been encrypted with?'
Use the following gpg2 command:
# gpg2 --list-only --decrypt <file name>
gpg2: encrypted with 1024-bit ELG-E key, ID 26787C6E, created 2001-11-01
"test <test@qvalent.com>"